The 4 Parts of Cybersecurity
August 17th, 2021 / By Jason Eckert
Simply put, Cybersecurity is an umbrella term that encompasses all aspects of computer, network and data security. While Cybersecurity-specific job roles are commonplace in larger organizations, smaller organizations often require that existing IT roles perform Cybersecurity-specific tasks. And since Cybersecurity is only going to grow in importance over time, anyone working in IT should have a solid knowledge of it.
Any IT professional should have a solid understanding of cybersecurity, as it will only grow in importance over time.
So what does Cybersecurity involve?
You can divide cybersecurity into four main areas today:
- Analysis: Inspecting the security of systems and networks by performing penetration testing and vulnerability assessments
- Administration: Implementing technologies and processes to harden the security of systems, networks, and data
- Response: Monitoring and reacting to security breaches
- Forensics: Performing post-mortem analysis of a security breach to identify the data accessed and the methods used by the attacker
Cybersecurity analysis
The main goal of Cybersecurity analysis is to test the security of existing systems. This often involves running detailed scans of systems and network traffic (called a vulnerability assessment or VA), as well as attacking existing systems to uncover security weaknesses (called a penetration test or pen test). The Cybersecurity professionals performing the attacks are called ethical hackers because they have permission from the organization to do so. A typical pen test and VA involves running several different tools from a Linux system, but can also involve social engineering (attempting to convince company employees to give up confidential information) and physical security tests (such as gaining access to an unauthorized area without detection). After a pen test and VA are performed, existing IT administrators are often tasked with fixing any security vulnerabilities found.
Cybersecurity administration
Cybersecurity administration is an area that nearly all IT professionals work with in some capacity. It involves locking down systems and data using a wide variety of different tools and software in order to minimize the chance that a hacker will gain unauthorized access. This often involves hundreds of different tasks, such as encrypting data, auditing permissions, implementing secure policies, requiring two-factor authentication (2FA), and providing secure backups of all data. Additionally, this area of Cybersecurity involves creating an Incident Response Policy (IRP) that can be followed in the event of a security breach. At minimum, the IRP must identify different types of security breaches possible as well as the steps that must be performed to contain the security breach, restore systems and data that provide Critical Business Functions (CBFs), and determine the root cause of the security breach.
Cybersecurity response
Cybersecurity response involves detecting and dealing with security breaches. While the detection of a security breach can be performed by anyone working in an IT job role, many organizations have dedicated cybersecurity job roles that monitor systems and networks to detect security breaches quickly, while others outsource this monitoring to third-party Cybersecurity companies. The person who detects a security breach is called a First Responder. Once detected, a Security Administrator tasks other IT administrators with carrying out the steps in the IRP, including restoring CBFs, determining the root cause of the breach, preparing data for a forensics team (discussed next), and documenting all relevant information.
Cybersecurity forensics
Cybersecurity forensics is the most specialized area of Cybersecurity, and involves examining information from a security breach in order to determine whether a hacker was able to access or steal data, as well as determine the method they used to compromise the security of the system. This often involves examining lists of processes and network sessions that are taken when the security breach is first discovered, as well as examining the contents of the compromised system’s hard drive. To ensure that the hard drive can be used as evidence in a legal proceeding, an image of the hard drive is taken and analyzed, while the original hard drive is locked in a cabinet alongside a form that identifies each time someone moved it (called a Chain of Custody). Recent backups of the system can also be used to aid in determining whether data was removed or manipulated.
Few smaller organizations have a dedicated Cybersecurity forensics team; they instead outsource any forensic analysis to third-party companies. Since this can be expensive, smaller organizations only perform forensics if required by law. For example, if a system that contained a database of personal customer information and passwords was breached, the company is required by Canadian law to disclose to affected customers what information was accessed by the hacker.
Regardless of whether forensics was involved in the security breach, a pen test and VA is often performed immediately afterwards to identify and fix any security vulnerabilities, thus reducing the chance that a similar attack will occur.
Putting it all together
The picture below details how all 4 areas of Cybersecurity work together in an organization, as well as illustrates a simple IRP (in green):
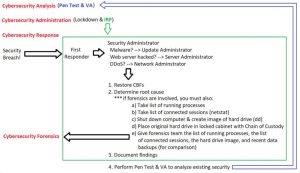
NOTE: Larger organizations often expand upon the tasks outlined above, as well as add more individual job roles within each area of Cybersecurity. For example, a Cybersecurity analysis job role in a larger organization may perform Threat Modeling on an ongoing basis to predict the likelihood of particular types of attacks based on global trends. Or those working in a Cybersecurity response job role may be required to perform regular drills that implement the tasks in an IRP, so that subtle improvements can be made that lower the time to recover from a future security breach.
Click to learn more about the Technology programs offered at Eastern!
Visit our Advanced Systems Management And Cybersecurity program page to learn more!
